Table of contents
- Drupal Security Vulnerabilities
- 1. Keep Calm and Stay Updated – Drupal Security Updates
- 2. Administer your inputs
- 3. Drupal 9 Security
- 4. Choose your Drupal modules wisely
- 5. Drupal Security Modules to the rescue
- Automatic Updates
- Login Security
- Two-factor Authentication
- Password Policy
- Username Enumeration Prevention
- Content Access
- Security Kit
- Captcha
- 6. Check on your Permissions
- 7. Get HTTPS
- Final Thoughts
Website security is not a set-it-and-forget-it task, but an ongoing process that needs constant attention. After all, it’s better to prevent a disaster than to respond to one. If you’re lucky enough to have a Drupal website, you at least have some assurance that the Drupal security team will resolve reported security issues swiftly and efficiently. But that’s just the first line of defense.
Drupal has powered millions of websites, many of which handle extremely critical data. Unsurprisingly, Drupal has been the CMS of choice for websites that handle high-security information like government websites, banking, and financial institutions, e-Commerce stores, etc. Drupal security updates and features address all top 10 security risks of OWASP (Open Web Application Security Project).
However, the onus is ultimately on you to ensure your website is secure by following security best practices and implementing continuously evolving security strategies. Read more to find out how.

Drupal Security Vulnerabilities
It goes without saying that the community takes security in Drupal very seriously and keeps releasing Drupal security updates/patches. The Drupal security team is always proactive and ready with patches even before a vulnerability goes public. For example, the Drupal security team released the security vulnerability update - SA-CORE-2018-002 days before it was actually exploited (Drupalgeddon2). Patches and Drupal security updates were soon released, advising Drupal site admins to update their websites.
Quoting Dries from one of his blogs on the security vulnerability – “The Drupal Security Team follows a "coordinated disclosure policy": issues remain private until there is a published fix. A public announcement is made when the threat has been addressed and a secure version of Drupal core is also available. Even when a bug fix is made available, the Drupal Security Team is very thoughtful with its communication.“
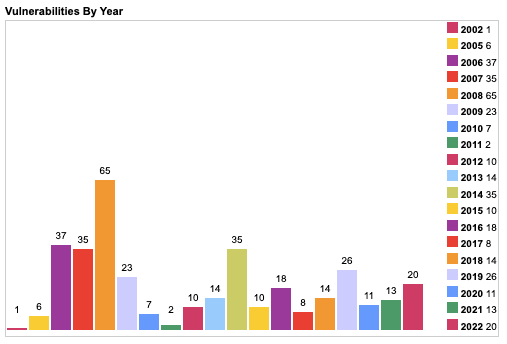
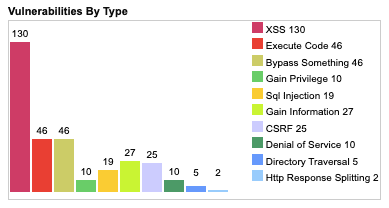
Some interesting insights on Drupal’s vulnerability statistics by CVE Details :
1. Keep Calm and Stay Updated – Drupal Security Updates
The Drupal security team is always on its toes looking out for vulnerabilities. Patches / Drupal security updates are immediately released as soon as they find one. Also, after Drupal 8 and the adoption of continuous innovation, minor releases are more frequent. This has led to easy and quick Drupal updates of a better, more secure version.
Making sure your Drupal version and modules are up-to-date is really the least you can do to ensure the safety of your website. Drupal contributors are staying on top of things and are always looking for any security threats that could spell disaster. Drupal updates don't just come with new features but also security patches and bug fixes. Drupal security updates and announcements are posted to users’ emails and site admins have to keep their versions updated to ensure security.
2. Administer your inputs
Interactive websites usually gather input from users. As website admins, unless you manage and handle these inputs appropriately, your website is at a high-security risk. Hackers can inject SQL codes that can cause great harm to your website’s data.
Stopping your users from entering SQL-specific words like “SELECT”, “DROP” or “DELETE” could harm the user experience of your website. Instead, with security in Drupal, you can use escaping or filtering functions available in the database API to strip and filter out such harmful SQL injections. Sanitizing your code is the most crucial step toward a secure Drupal website.
3. Drupal 9 Security
How is Drupal 9 helping in building a more robust and secure website?
- Symfony – With Drupal 8 adopting the Symfony framework, it opened doors to many more developers other than limiting them to just core Drupal developers. Not only is Symfony a more secure framework, but it also brought in more developers with different insights to fix bugs and create security patches.
- Twig Templates – As we just discussed sanitizing your code to handle inputs better, here’s to tell you that with Drupal, it has already been taken care of. How? Thanks to Drupal 8’s adoption of Twig as its templating engine. With Twig, you will not need any additional filtering and escaping of inputs as it is automatically sanitized. Additionally, Twig’s enforcement of separate layers between logic and presentation, makes it impossible to run SQL queries or misuse the theme layer.
- More Secure WYSIWYG - The WYSIWYG editor in Drupal is a great editing tool for users but it can also be misused to carry out attacks like XSS attacks. With Drupal 9 following Drupal security best practices, it now allows for using only filtered HTML formats. Also, to prevent users from misusing images and to prevent CSRF (cross-site request forgery), Drupal’s core text filtering allows users to use only local images.
- The Configuration Management Initiative (CMI) – This Drupal initiative works out great for site administrators and owners as it allows them to track configuration in code. Any site configuration changes will be tracked and audited, allowing strict control over website configuration.
4. Choose your Drupal modules wisely
Before you install a module, make sure you look at how active it is. Are the module developers active enough? Do they release Drupal security updates often? Has it been downloaded before or are you the first scapegoat? You will find all the mentioned details at the bottom of the modules’ download page. Also, ensure your modules are updated and uninstall the ones that you no longer use.
5. Drupal Security Modules to the rescue
Just like layered clothing works better than one thick pullover to keep warm during winter, your website is best protected in a layered approach. Drupal security modules can give your website an extra layer of security around it.
Automatic Updates
This is currently a contributed module but will soon move to core in Drupal 10. The goal of the automatic updates initiative is to provide an easy, safe and secure way to update a Drupal website automatically. It helps automatically update your site with core patches and security releases. Any issues during the update process are detected and reported so you don’t have to find out later.
Login Security
This module ensures security in Drupal by allowing the site administrator to add various restrictions on user login. The Drupal login security module can restrict the number of invalid login attempts before blocking accounts. Access can be denied for IP addresses either temporarily or permanently.
Two-factor Authentication
With this Drupal security module, you can add an extra layer of authentication once your user logs in with a user-id and password. Like entering a code that’s been sent to their mobile phone.
Password Policy
This is a great Drupal security module that lets you add another layer of security to your login forms, thus preventing bots and other security breaches. It enforces certain restrictions on user passwords – like constraints on the length, character type, case (uppercase/lowercase), punctuation, etc. It also forces users to change their passwords regularly (password expiration feature).
Username Enumeration Prevention
By default, Drupal lets you know if the username entered does not exist or exists (if other credentials are wrong). This can be great if a hacker is trying to enter random usernames only to find out one that’s actually valid. This module enables security in Drupal and prevents such attacks by changing the standard error message.
Content Access
As the name suggests, this module lets you give more detailed access control to your content. Each content type can be specified with custom view, edit or delete permissions. You can manage permissions for content types by role and author.
Security Kit
This Drupal security module offers many risk-handling features. Vulnerabilities like cross-site scripting (or sniffing), CSRF, Clickjacking, eavesdropping attacks, and more can be easily handled and mitigated with this Drupal 9 security module.
Captcha
As much as we hate to prove our human-ness, CAPTCHA is probably one of the best Drupal security modules out there to filter unwanted spambots. This Drupal module prevents automated script submissions from spambots and can be used in any web form of a Drupal website
6. Check on your Permissions
Drupal allows you to have multiple roles and users like administrators, authenticated users, anonymous users, editors, etc. In order to fine-tune your website security, each of these roles should be permitted to perform only a certain type of work. For example, an anonymous user should be given the least permissions like viewing content only. Once you install Drupal and/or add more modules, do not forget to manually assign and grant access permissions to each role.
7. Get HTTPS
I bet you already knew that any traffic transmitted over just an HTTP could be snooped and recorded by almost anyone. Information like your login id, password, and other session information can be grabbed and exploited by an attacker. If you have an e-Commerce website, this gets even more critical as it deals with payment and personal details. Installing an SSL certificate on your server will secure the connection between the user and the server by encrypting the data that’s transferred. An HTTPS website can also improve your SEO ranking – which makes it totally worth the investment.
Final Thoughts
As the old adage goes - Expect the best but plan for the worst. By default, Drupal is a very secure content management framework, but you will still need to implement security strategies and follow Drupal security best practices for a good night’s sleep. Drupal 9 brings along a whole new bunch of security features for a more robust and secure website. Nonetheless, keeping your website up-to-date with Drupal security updates is indispensable. Writing clean and secure code plays a significant role in your website security. Choose an expert Drupal development agency that can provide you with effective security strategies and implementation services.